You’ve just taken over as an information security director, manager, or architect at an organization. Either this is a new organization that has never had this role before or your predecessor has moved on for some reason. Now what? The following outlines steps that have been shown to be effective (also based on what’s been ineffective) getting traction and generating results within the first three months. Once some small successes are under your belt, you can grow the momentum to help the business grow faster or reduce the risk to their success (or both).
Now what do we do?
Apply a tried and true multi phase approach .. assess current state, determine desired target state, perform a gap analysis, implement improvements based on priority. Basically we need to establish current state, determine what future state should be, and use the gap analysis as the deliverables of the IT security program. There may be many trade-offs that are made due to limiters like political challenges, funding constraints and difficulty in changing corporate culture. The plan you build with the business gives you the ammunition needed to persuade all your stakeholders of the value in the changes you’ll be proposing.
1. Understand the Current Environment
For a manager or enterprise architect to determine where to start, a current state must be known. This is basically an inventory of what IT security controls, people and processes are in place. This inventory is used to determine what immediately known risks and gaps from relevant security control frameworks exist. The known risks and gaps gives us a starting point to understand where impacts on the business may originate from.
Take the opportunity to socialize foundational security concepts with your new business owners and solicit their input. What are the security related concerns they have? If there has been any articulation of Strengths, Weaknesses, Opportunities, and Threats (SWOT), obtaining that review can also give you an idea of weaknesses or threats that are indicative of missing controls. In the discussions with your new constituents, talk to the infrastructure managers and ask them what security related concerns keep them awake at night – there is likely some awareness but they don’t know how to move forward. Keep in mind most organizations will want a pragmatic approach versus an ivory tower perfect target state.
Some simple questions can quickly give you a picture of the state of security controls. For example, in organizations I’ve worked with, the network administrators could not provide me a complete “layer three” diagram – a diagram that shows all the network segments and how they hang together. It wasn’t that they didn’t want to, the diagrams simply didn’t exist. With over 1,500 network nodes over two data centers and two office complexes, the network group had the topology and configuration “in their heads”. Obvious weaknesses and threats include prevention of succession planning or disaster recovery, poor security transparency, and making nearly any change to the environment higher risk than necessary.
Another example is an organization that had weak asset control. At any point in time it was nearly impossible to determine if unauthorized network nodes existed, since the workstation, notebook, server, virtual machine, switches, firewalls, printers and any other network connected equipment were tracked separately, if at all. No regular audits were performed to reconcile what the organization had purchased was actually what was connected to their networks. This points to weak change control and weak asset control. Without strong asset control, it is difficult to offer assurance to the business owners that serious vulnerabilities have been mitigated to a level they can accept.
Ensure you’re asking questions that will allow you to develop future metrics, such as:
- Do security controls that are in place generate measurable performance statistics?
- How many user accounts are added, disabled, deleted per day/week/month/quarter?
- What volume of inbound email is spam/malware?
- Does the operations team have baselines of normal network, system, application activity?
- Profile of user accounts – how many are inactive (say 90 days)
- How automated is the new hire, dehire, change process? Is there room for manual error?
- How many administrator accounts are there (percentage of all accounts)
- What degree of individual user accountability is there? Are there signed acceptable use agreements?
- Are there accurate network topology and security zone as-built diagrams?
- Is there clear segregation of assets that contain high value data?
- Are content filtering and malware controls deployed?
All these identified issues can then be dropped into a mind map or even a spreadsheet to visualize the highest risks. More on this in a minute.
2. Determine Target State
Next there must be a clear understanding of business goals, since IT (and IT security) always needs traceability back to the goals of a business. Application of good architecture practice then leads to being able to generate a ‘future state’ and a gap analysis. You don’t have time for a full heavy weight analysis, so a good place to start here is to identify what external regulatory compliance mandates exist – there likely are multiples. For example, financial integrity and reporting requirements (SOX / CSOX / JSOX / GLB / Basel / PCI-DSS), privacy (CA-SB-1384, PIPA), critical infrastructure (NERC CIP), government IT systems (FISMA), and health records (HIPAA). Over and above the external regulatory requirements, there may also be a requirement for voluntary or internal compliance mandates, such as corporate policy compliance.
Keep in mind that where a framework like ISO 27002 or NIST SP 800-53 is used, there may be some latitude. For example, your organization may decide that some controls in the framework are not applicable, and exclude them. So a “C” or “C+” may be as good as your organization wants to get. That’s ok, as long as it’s a concerted decision and you can still hit your mandatory targets.
This is an area where there may a need for substantial effort, so using a common security control framework like ISO 27002 or NIST 800-53 can give a somewhat logical progression of capability maturity that you can build on to close the gaps and start to get a better foundation in place that allows your IT security program to be sustainable. The other benefit to getting to know a good framework is that many compliance mandates are attainable by using the controls in these frameworks – although you may need to adjust a little here or there. The frameworks also act as a checklist for areas to ensure are addressed adequately for your organization.
While using your chosen control framework, also consider a capability maturity level, such as what is outlined in the Carnegie Mellon software Capability Maturity Model (CMM). Where you find deficiencies, choosing controls and configurations that phase in a new control gradually over some predetermined period of time versus expecting a sudden transition from low capability to high capability allows the organization to adapt and culturalize the new controls.
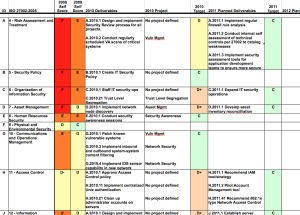 I would suggest using the control framework categories so you can cross reference the issues you’ve uncovered to controls in the framework – you’ll use this to help triage what needs to be focused on first, while helping to capture that data in a way you’ll use for the long term plan.
I would suggest using the control framework categories so you can cross reference the issues you’ve uncovered to controls in the framework – you’ll use this to help triage what needs to be focused on first, while helping to capture that data in a way you’ll use for the long term plan.
3. Assess Highest Risks and Identify Operational Wins (gap analysis)
A successful security plan includes executive endorsement of policy, standards, procedures and guidelines. That said, start with the highest risks you identified in step one. Especially the risks that have simple or inexpensive controls that would work. Remember to integrate metrics where possible to enable feedback and improvement. See www.securitymetrics.org for examples of good metrics.
Ensure you are improving:
- Situational awareness (logging, monitoring, reporting and visibility)
- Response capability to Computer Security Incidents
- Long term security controls (build the foundation so you’re not always fighting fires)
There are several assessment methodologies available, including the NSA IAM, Canadian RCMP TRA and Open Source Risk Assessment toolkits and methodologies.
4. Implement Controls to Mitigate Risks
Long term you want to introduce a way to reduce the daily crisis response, by building up the foundational maturity of the organization’s security controls. Short term you need to get some of the major issues and exposures fixed.
 Finally changes to process and possibly organization can complete the ability of IT security to stay evergreen (sustainable). Once you’ve made some changes to the environment, it’s important to ensure there is management metrics and process implemented to sustain the changes you’ve made. For instance, if an asset inventory has been done, the value of that goes out the window if there is no measurable, enforceable process to keep the inventory accurate.
Finally changes to process and possibly organization can complete the ability of IT security to stay evergreen (sustainable). Once you’ve made some changes to the environment, it’s important to ensure there is management metrics and process implemented to sustain the changes you’ve made. For instance, if an asset inventory has been done, the value of that goes out the window if there is no measurable, enforceable process to keep the inventory accurate.
Work the evaluation process with your stakeholders and senior management to ensure you are building your roadmap with their support. Laying out a long term plan and showing where you are in the plan will allow you to get increased executive buy-in for more expensive and possibly organizational changes.
You will find that the focus on issues, from whatever source they have been discovered (Architecture Assessments through actual Security Incidents), will tend to be on the highest criticality. This will result in projects or funding for efforts to close a particular issue or exposure – but still results in fire-fighting. You need over the term of your 90 days to ensure you socialize the IT Security Program framework that includes short-term fire-fighting (Urgent) -AND- long term (Foundational) work. This is more than a simple compliance mandate, since companies can be fully compliant with all regulatory mandates, but still get pwned. A rational application of a framework like ISO 27002 or NIST SP 800-53 can result in compliance success and good security.
You will be presented with “stakeholders” that insist on massively grand Total Cost of Ownership (TCO) or foundational Security Policy work, but you must resist such efforts that will undermine and ultimately defeat good security.
This is a plan that I’ve found helpful to survive the first 90 days and possibly build and maintain a positive working relationship with your senior management as they see value in the IT security program. At that point you will have an IT security program that actually works for the organization and is cost effective.
5. Publish a Schedule of Audits
Once some of the foundational controls are in place, gain acceptance and buy-in from your constituents through the use of a well known internal audit schedule. This will help to confirm the effectiveness of steps 1 through 4 and helps in reducing the amount of effort required to perform audits for regulatory mandate compliance proof. In some cases, you may be able to combine these audits, although what you are trying to do here is ensure all the controls you have put into place are functioning as expected, while external audits may not go that deep.
Once you have these steps in place, your security posture will improve and you will experience less fire-drills around suspected incidents.
